Security Configuration Manager is an attack surface reduction tool for Windows Server 2008 SP2. It determines the minimum functionality required for a server’s role, and disables functionality that is not required. SCW does the following:
· Disables unneeded services
· Blocks unused ports
· Allows further address or security restrictions for ports that are left open
· Prohibits unnecessary IIS web extensions, if applicable
· Reduces protocol exposure to server message block (SMB), LanMan, and Lightweight Directory Access Protocol (LDAP)
NOTE: When using this procedure you must be aware that different options within ‘Security Configuration Manager’ will be required depending on the type of server you are building. This procedure details the configuration for the OCS EDGE servers only.
· To harden the server, the Security Configuration Wizard (SCW) needs to be run which allows you to create a security policy to be applied.
· Logon to the OCS EDGE server with the local admin account and launch Security Configuration Wizard via Administration Tools.
· Select Next (click OK on the Access denied prompt)
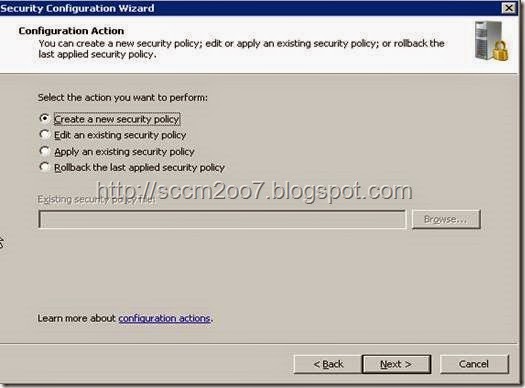
· Select Create a new security policy and Next
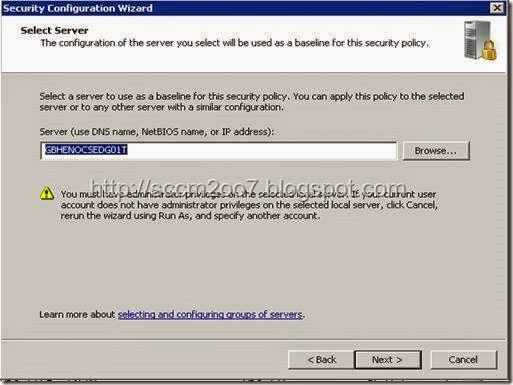
· Add the server name you are applying the Security policy to and click Next.
· Next of the resulting screen.
· Next again.
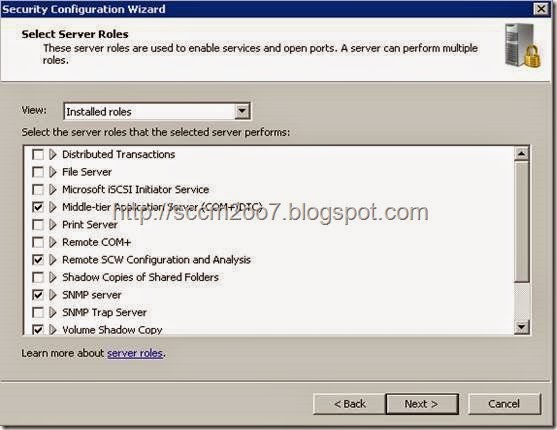
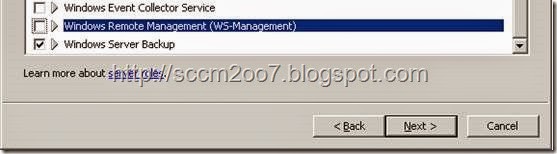
· Ensure the following installed roles are selected and click Next.
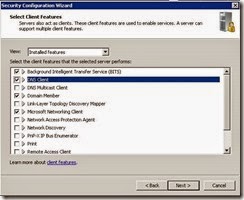
· Ensure the following installed features are selected and click Next.
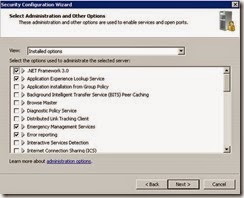
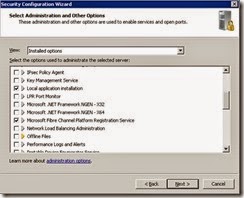
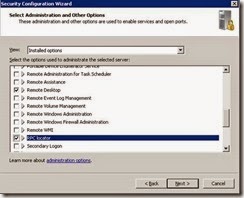
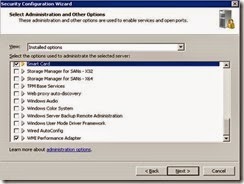
· Ensure the following installed options are selected and click Next.
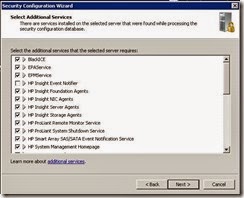
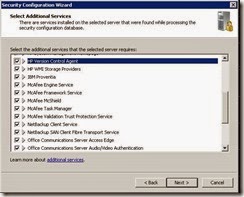
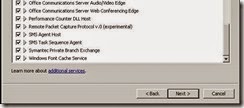
· Ensure the following additional services are selected and click Next
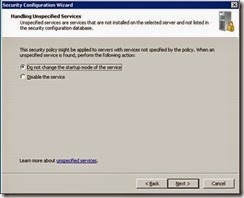
· Take the default option handling unspecified services and click Next.
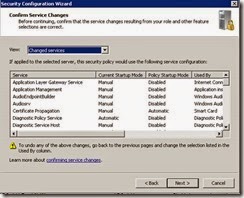
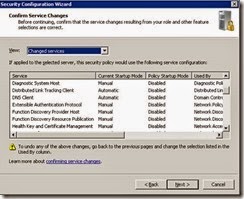
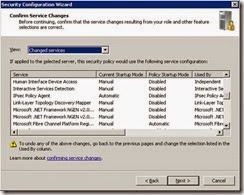
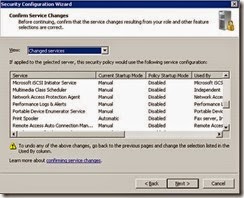
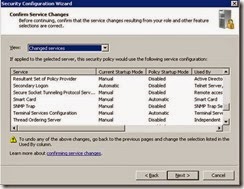
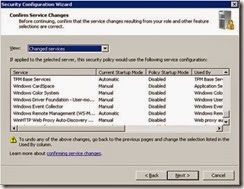
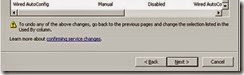
· Review the following services as per the screenshots. (DNS client is now enabled so will not appear)
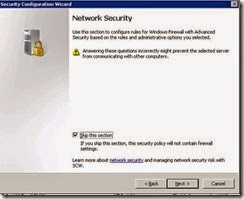
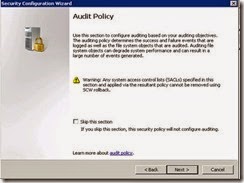
· Select Skip this section and Next.
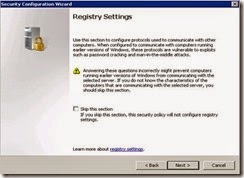
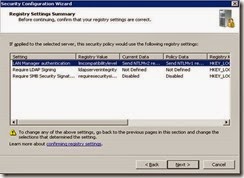
· On Registry setting click Next.
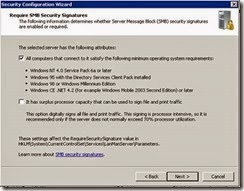
· Deselect - It has surplus processor capacity etc and click Next.
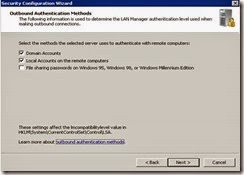
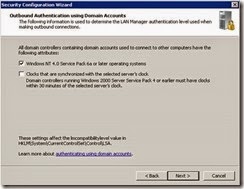
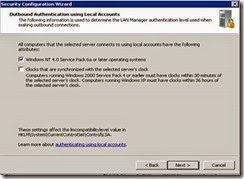
· Select Local Accounts on the remote computers option in addition to Domain Accounts and click Next.
· Take the default option on the next four screens and click Next four times.
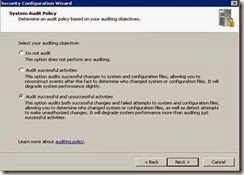
· Select Audit successful and unsuccessful activities and click Next.
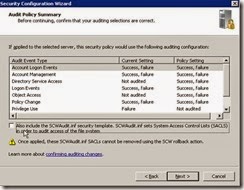
· Deselect the option to include the SCWAudit.inf security template and click Next.
· Click Next to save the policy.
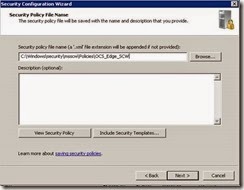
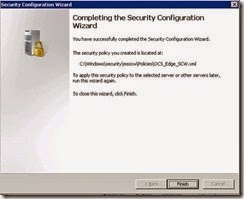
· Create the policy name OCS_Edge_SCW and click Next.
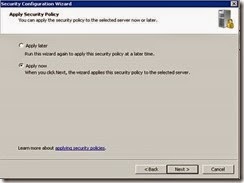
· Click apply now and Next.
· Click Next once the policy has been applied
· Click Finish.

No comments:
Post a Comment